970x125
It usually starts with a harmless web search. You are attempting to locate a website for a product that you really liked, and as you click on the link, a familiar box pops up, asking you to prove you are not a robot. You see “I’m not a robot” written, and the checkbox. You have seen it so many times, so you don’t really give it much thought.
970x125
Sometimes, this could be a trap. One wrong click, and instead of proving you’re human, you could be opening the door to malware, and behind this, is a fake CATCHA scam.
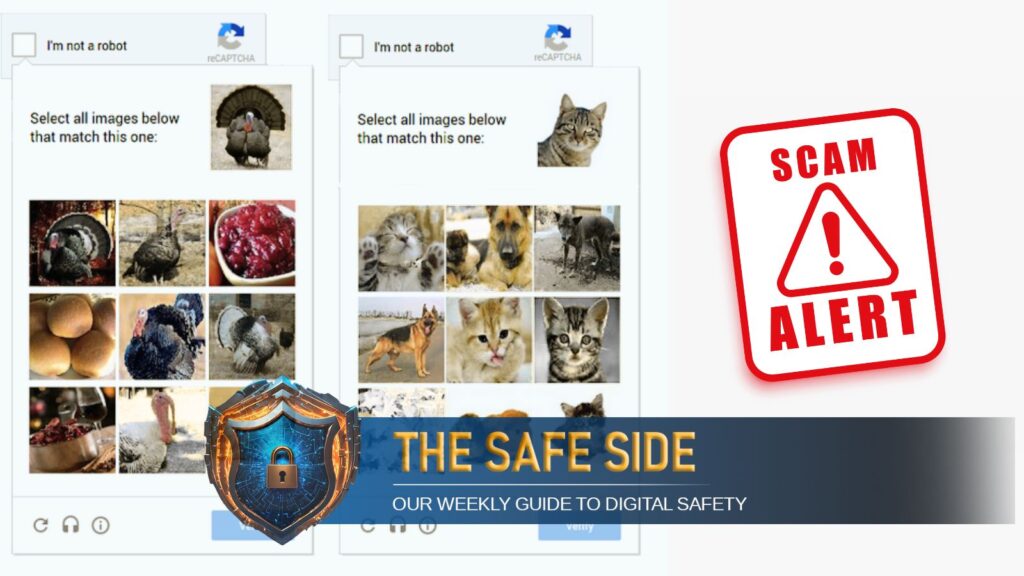
What is a CAPTCHA?
CAPTCHA stands for “Completely Automated Public Turing test to tell Computers and Humans Apart.” It’s a security tool to confirm a user is human, not a bot.
CAPTCHAs may involve distorted text, image selection, audio cues, simple puzzles, or just ticking a checkbox (called reCAPTCHA). These may also be time-based.
What is a fake CAPTCHA scam?
Cybercriminals now mimic these tests to trick users into downloading malware.
“Fake CAPTCHAs are often distributed through compromised websites, malicious ads, or phishing emails,” said Zakir Hussain Rangwala, CEO of BD Software Distribution Pvt Ltd. “They may also appear on lookalike domains of popular sites, persuading users to enable browser notifications or download files under the guise of verification.”
According to CloudSEK’s Threat Research and Information Analytics Division (TRIAD), “A sophisticated tactic is being used to spread the Lumma Stealer malware, targeting Windows users through fake human verification pages.”
CloudSEK found that in this campaign, threat actors create phishing sites hosted on various providers, often leveraging Content Delivery Networks (CDNs) for faster distribution and added legitimacy. These sites display a counterfeit Google CAPTCHA page, designed to mimic the real verification process. These phishing sites instruct users to:
* Open the Run dialog (Win+R)
* Press Ctrl+V
* Hit Enter
Story continues below this ad
This action executes a hidden JavaScript function that copies a base64-encoded PowerShell command to the clipboard, and this, when executed, downloads the Lumma Stealer malware from a remote server.
“Clicking a fake CAPTCHA itself isn’t the real danger; the problem begins when you follow the instructions it provides. For example, pasting commands into your terminal and executing them, or downloading a file to “prove” you’re not a robot, can put you at serious risk. Always avoid carrying out such instructions,” said Anshuman Das, cybersecurity researcher at CloudSEK.
How can an average user differentiate between a real and a fake CAPTCHA?
Deependra Singh, cyber expert, Betul Police (MP), and Rangwala outlined key differences between genuine and fake CAPTCHAs.
Legitimate CAPTCHAs appear on trusted websites and involve straightforward tasks such as selecting images, entering distorted text, or ticking a checkbox. Fake ones, on the other hand, often demand unrelated actions like clicking “Allow” for notifications, downloading files, or providing personal or financial information. A quick way to spot a fake is to check the site’s address for misspellings, unusual characters, or unfamiliar domains. Another red flag is if the CAPTCHA appears as a random pop-up rather than being embedded directly within the webpage.
What to do if you suspect you have encountered a fake CAPTCHA
📌Exit the site immediately.
📌Disconnect from the internet.
📌Run a full antivirus scan.
📌Clear browser cache and cookies, and remove suspicious extensions.
📌Change passwords for critical accounts using a secure device.
📌Delete any downloaded files without opening them.
Story continues below this ad
“Industries like e-commerce and online gaming face higher risks,” Rangwala warned. “These attacks can steal credentials, install spyware, or allow remote access.”
Singh’s advice is simple: “Avoid clicking unknown links and always check the URL. One wrong click can cost you both your money and your privacy.”
970x125